The Significance of Cyber Safety And Security in Protecting Your Digital Possessions
In today's electronic era, the significance of cyber protection in safeguarding your digital possessions can not be overemphasized. As innovation advancements, so do the tactics of cybercriminals, making durable cyber defenses vital for individuals and services alike. From personal data to important service info, the risk landscape is large and ever-changing. Carrying out effective cyber protection techniques is not just a referral yet a need to ensure and reduce risks continuity. What methods can you adopt to stay one action in advance and fortify your digital existence against these consistent hazards? The solutions could stun you.
Comprehending Cyber Hazards
In the quickly developing landscape of electronic modern technology, recognizing cyber threats is extremely important for guarding electronic assets. The term "cyber hazards" incorporates a broad variety of harmful activities aimed at endangering the honesty, discretion, and availability of information systems. These threats range from malware, phishing, and ransomware assaults to a lot more innovative exploits like zero-day susceptabilities and Advanced Persistent Threats (APTs) Each type of threat exhibits special features, targeting details weaknesses within digital systems, usually with the intent to take information, interrupt procedures, or need ransom money.

Understanding the motivations behind these dangers-- be it economic gain, reconnaissance, or hacktivism-- is essential for creating reliable countermeasures. This expertise equips organizations to anticipate prospective risks, tailor their defenses, and inevitably shield their beneficial electronic properties from cyber adversaries.
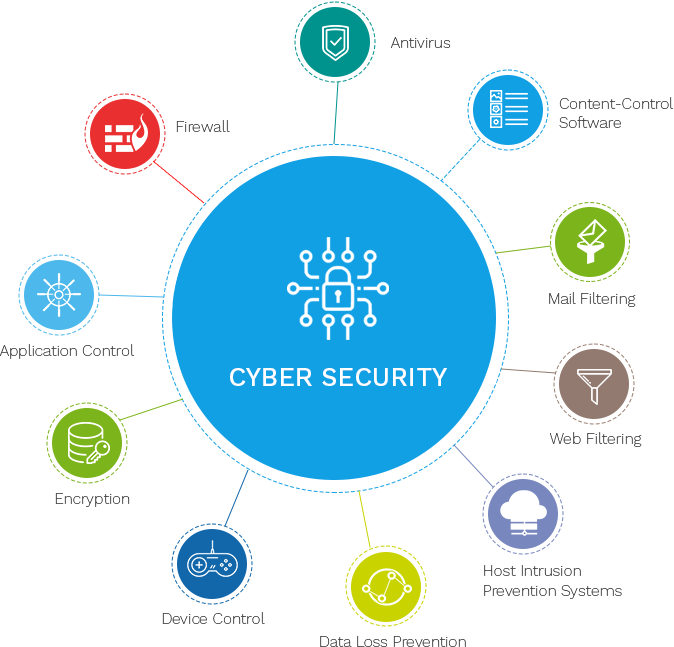
Secret Cyber Security Practices

Network safety is an additional important element - Best Cyber Security Services in Dubai. This entails the use of firewall programs and intrusion detection systems to keep an eye on and control incoming and outbound network traffic, successfully obstructing dubious tasks. Frequently upgrading software program and systems is equally crucial, as it covers known vulnerabilities that cybercriminals can make use of
Information security is a critical practice that makes sure delicate details is just accessible to licensed individuals. By transforming information right into a code, it ends up being unreadable without the decryption trick, hence shielding it from unapproved accessibility throughout transmission or storage space.
Enlightening staff members and customers concerning cyber protection ideal techniques is additionally essential - Best Cyber Security Services in Dubai. Regular training sessions can elevate recognition regarding typical risks like phishing and social engineering, empowering individuals to recognize and stay clear of possible dangers. By integrating these essential practices, companies can develop a durable defense versus the ever-changing landscape of cyber hazards
Protecting Personal Information
Protecting personal data try this has actually ended go up being a critical in today's electronic age, where the volume of info exchanged online is staggering. This information includes whatever from social safety numbers to personal health documents, and its security is important for maintaining personal privacy and protection. Individuals must be cautious in making sure that their personal information is not endangered, as breaches can bring about identity theft, monetary loss, and reputational damage.
Understanding of phishing attempts is critical, as cybercriminals regularly utilize deceptive e-mails and sites to steal individual details. Individuals must confirm the source of unsolicited interactions and prevent clicking questionable links. Finally, protecting individual gadgets with anti-virus software application and firewalls can better fortify defenses versus unauthorized accessibility and prospective risks.
Safeguarding Service Information
While securing personal data stays a concern for individuals, companies face the broader helpful site challenge of protecting large amounts of sensitive details that drive their procedures. Applying durable cyber safety procedures is not just an alternative but a critical requirement for services of all sizes.
To efficiently protect business information, a multi-layered protection strategy is crucial. This ought to encompass firewalls, security, invasion detection systems, and regular protection audits. Furthermore, employee training plays a significant duty in lessening human errors, which are often exploited in cyber-attacks. Firms should grow a security-conscious society where employees recognize the value of data security and are geared up to identify phishing attempts and various other dangers.
In addition, companies must develop and on a regular basis upgrade incident action strategies. Being planned for prospective violations ensures swift action to alleviate damages. By purchasing comprehensive cyber safety approaches, businesses not only safeguard their possessions however additionally enhance trust with their partners and clients, eventually protecting their market placement and future development.
Future Fads in Cyber Protection
As the digital landscape rapidly advances, future fads in cyber safety and security are poised to redefine just how services safeguard their digital properties. These innovations enable much faster identification of abnormalities and prospective threats, permitting for much more automated and reliable actions to cyber incidents.
An additional considerable fad is the growing focus on zero-trust design. As remote job ends up being more common, traditional perimeter-based protection designs are proving poor. The zero-trust approach calls for continuous confirmation of tools and users, also within the network, thereby lessening possible assault vectors. This change is important for safeguarding modern, dispersed IT settings.
Additionally, quantum computer is becoming both a possibility and a danger. While it assures unmatched handling power, it poses risks to present file encryption techniques. Organizations needs to plan for post-quantum cryptography to guard their information.
Last but not least, privacy-enhancing technologies are acquiring momentum. With enhancing regulative concentrate on data security, companies are purchasing tools that guarantee compliance while maintaining functional performance. These future fads emphasize the vibrant and ever-evolving nature of cyber safety.
Final Thought
In a progressively interconnected digital landscape, the implementation of durable cyber protection actions is necessary to guard digital assets from evolving dangers such as phishing, malware, and ransomware. Employing practices like solid passwords, multi-factor authentication, and regular software program updates boosts the security of sensitive info, mitigating dangers of identification theft and financial loss. Structure understanding and adopting innovative protection methods foster resilience and trust fund, making sure the integrity and connection of both personal and business digital operations despite future cyber obstacles.
In today's digital period, the relevance of cyber protection in safeguarding your digital properties can not be overstated.Implementing efficient cyber security methods is critical in securing digital possessions against progressing threats.As the digital landscape swiftly develops, future patterns in cyber safety and security are positioned to redefine how services shield their digital possessions.In an increasingly interconnected digital landscape, the execution of robust cyber safety and security actions is important to secure electronic possessions from advancing risks such as ransomware, phishing, and malware. Building understanding and embracing innovative security techniques foster durability and trust fund, ensuring the integrity and continuity of both personal and company digital procedures in the face of future cyber obstacles.